Building a Resilient Supply Chain Through Proactive Security Planning
Why early risk assessment, layered security measures, and data-driven planning are essential for building resilient supply chains
Why early risk assessment, layered security measures, and data-driven planning are essential for building resilient supply chains
As globalization evolves, supply lines between businesses, countries, and types of transportation become ever more interdependent - both efficient and opening up more opportunities - but also vulnerable to theft, tampering, counterfeiting, natural disasters, or human error. Too often, businesses respond only when something goes wrong, resulting in both financial losses and reputational damage. Planning would have given more resilience against such mishaps.
Supply chains must operate quickly and efficiently while remaining functional when problems arise unexpectedly. To achieve this goal, businesses need to plan, identify risks early, and create processes that reduce the likelihood of problems.
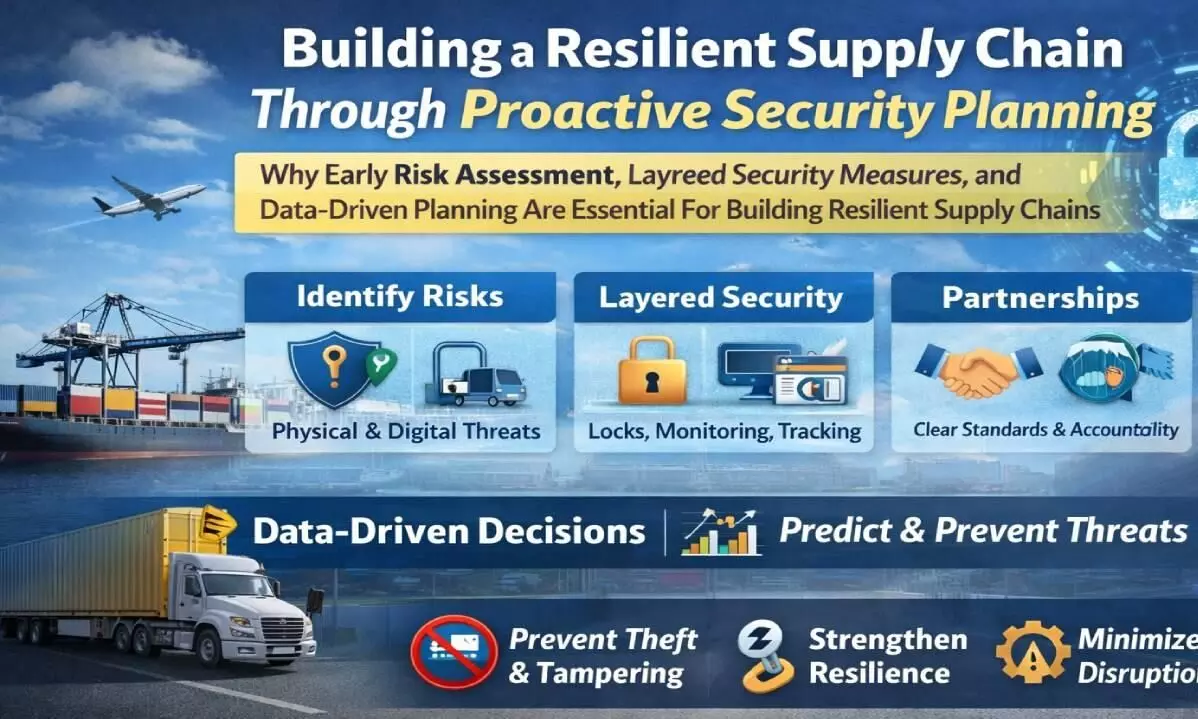
Understanding Risk Across the Entire Chain
An integral component of strategy planning is understanding risk throughout your supply chain. Too often, businesses only think about security when shipping long distances by boat or truck - yet risks lurk everywhere - from warehouses, distribution centers, cross-docking facilities, and last-mile delivery routes to warehouses, distribution centers, and cross-docking facilities - companies should carefully consider potential threats before making long-term plans and mapping out how their goods have traveled from creation to delivery. A roadmap can also help uncover any gaps that require additional research.
Businesses should carefully assess both physical and digital threats when determining the risk they pose. Examples of physical risks include theft, unauthorised entry, or tampering with goods, while data breaches or tracking system failure can pose digital risks that could significantly disrupt operations. When considering both sides simultaneously, businesses gain a clearer view of any gaps that could impede progress and how to overcome them.
Designing Layered Security Measures
For optimal security, multiple measures must be used simultaneously to keep packages safe. Locks, monitoring systems, and controlled entry points are effective physical deterrents when used in accordance with strict rules and supported by tracking technology.
Devices that cannot be changed are essential components of a layered method. Other tools, such as Red flag seals, can help locate containers or trailers that have been opened without permission and quickly provide evidence of breaches. When combined with electronic tracking and document checks, such devices provide an effective barrier against tampering during transit.
Strengthening Partnerships and Accountability
Logistics operations involve numerous people working together, from carriers and warehouse owners to customs officers and third-party logistics providers. If any link in the chain breaks, everything could become vulnerable. This requires partners to agree on clear standards and implement them together for effective, proactive security planning.
All parties involved in a supply chain can work together to ensure safety through contracts, audits, and training programs. At their peak performance, supply chains operate most effectively when everyone knows exactly how they must act to handle matters correctly. Record any suspicious behavior immediately so losses don't occur due to unreported issues or unexpected patterns of conduct.
Using Data to Stay Ahead of Threats
Data has become an integral component of supply chain security in modern business environments. Tracking tools, route analytics, and incident logs all provide valuable insights into risk. When incidents occur more frequently on certain roads or at specific locations, businesses can adjust their security measures or implement additional controls.
Predictive analytics enables businesses to stop reacting to issues and start preventing them before they occur, such as theft or tampering. By studying trends, businesses can identify potential problems and address them before they occur.
Building a Culture of Security
Maintaining safety should become part of everyday life. More than technology or tools alone, workers are essential in keeping people safe - managers, drivers, and storage workers must all know and follow safety rules for maximum success. Training programs that explain why certain steps are needed will attract greater interest than those that simply list steps.
To increase early detection, one effective approach is to ensure people can report suspicious activities without fear of retaliation from authorities or others. Furthermore, encouraging people to address small problems promptly before they worsen is another approach; by staying alert and acting swiftly when issues arise, they'll be less likely to let minor issues escalate over time.
Conclusion
For supply chains to function effectively, careful planning and construction are required. Companies can stay ahead of potential threats by carefully evaluating risks across all supply lines, implementing multiple layers of security controls, and working closely with their providers to make data-driven decisions. When security plans are implemented early, supply chains can shift from weak systems that struggle to cope with daily issues to strong networks that can withstand sudden shocks.

